Is Click Fraud Funding Terrorism?
synopsis
This article examines the links between online advertising through large US corporations and the practice of click fraud. Foreign nationals appear to be using American companies to defraud legitimate advertisers and funnel money to unknown individuals or groups in the Middle East.
content
How click fraud works
Whenever you advertise online, you hope that your dollars are well spent. You believe that large corporations have technology in place to ensure that you’re not being defrauded. You may even have your own system that tries to detect automated clicks, or robots, trying to drain your ad account.
All of that is well and good — but what if there was a way to steal your money using real people? What if I could pay someone 13¢ to steal $3 from you over and over?
Well, there is. That’s the exact premise behind click fraud using crowdsourced microworkers.

There are websites where you can hire microworkers from all over the world to perform small tasks like searching and clicking on websites and ads.
Because microworkers are real people on real computers performing real searches for small sums of money, there is no way for your automated systems to spot and eliminate this fraudulent activity. They click and you pay. It’s that simple. The money is then neatly funneled into the fraudster’s account and you’re none the wiser.
Let’s take a look at a real-world example of how this is being done as of the publishing date of this article.
Real world example of personal injury lawyers being defrauded
The examples below are screenshots outlining the microworker process used to conduct searches and clicks on lawyer advertising. The reason the fraudsters are targeting this industry is because it’s a very competitive field with high cost-per-click (CPC) prices.
The scammer is able to pay his workers pennies in order to steal dollars. This kind of click fraud is also called search arbitrage. Traditionally it could, and still is, being done by paying a little money for ads which then result in higher payouts from the ad clicks on the hosting site. The advertiser then makes the difference on the spread between what he paid and what he got for the ad click on his site.
The difference between arbitrage and click fraud is that the workers in this example have no interest in obtaining legal services, and are only performing the action in order to be paid for the activity of clicking. It’s plain robbery.
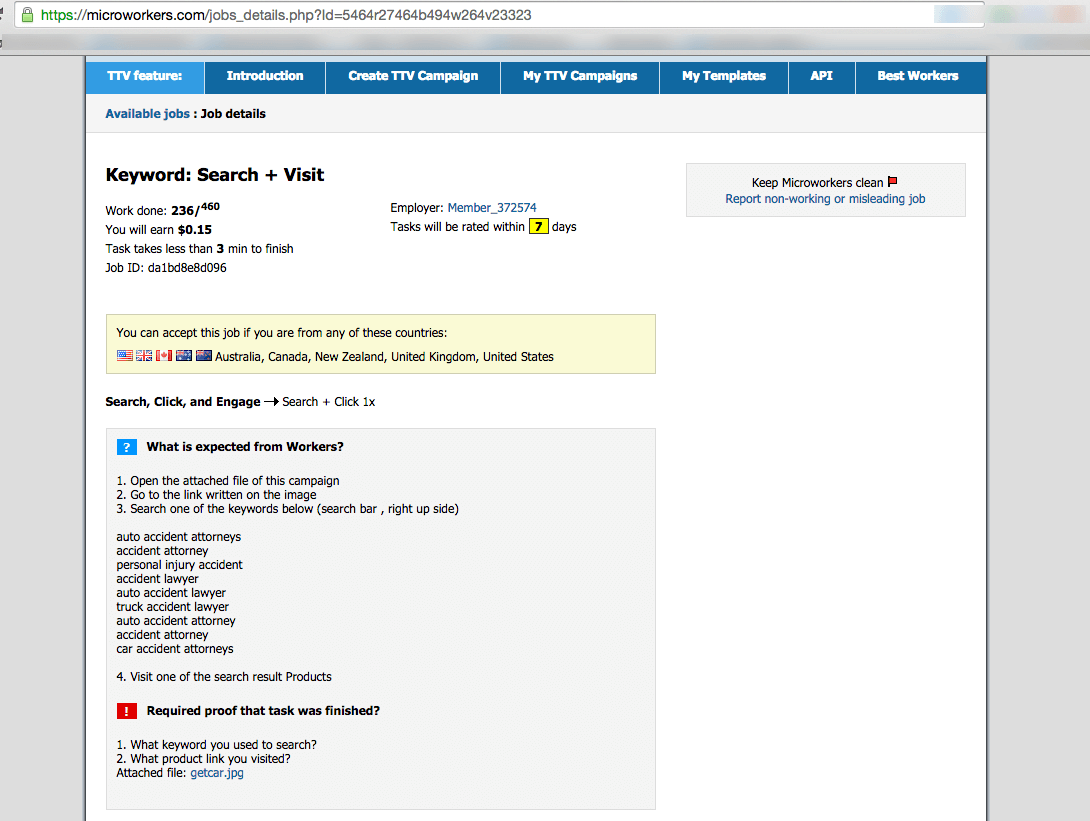
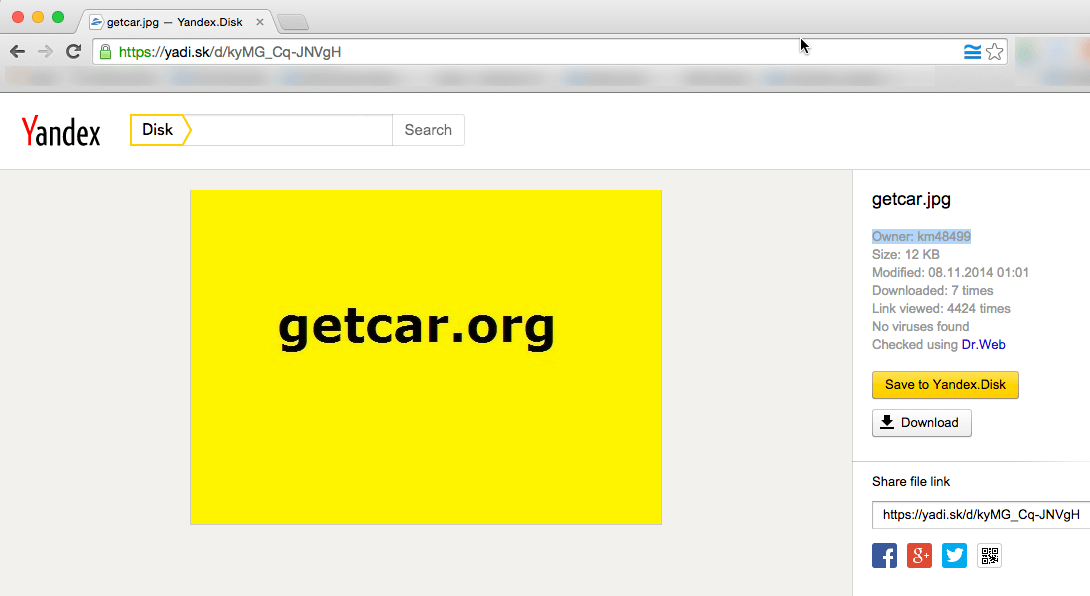
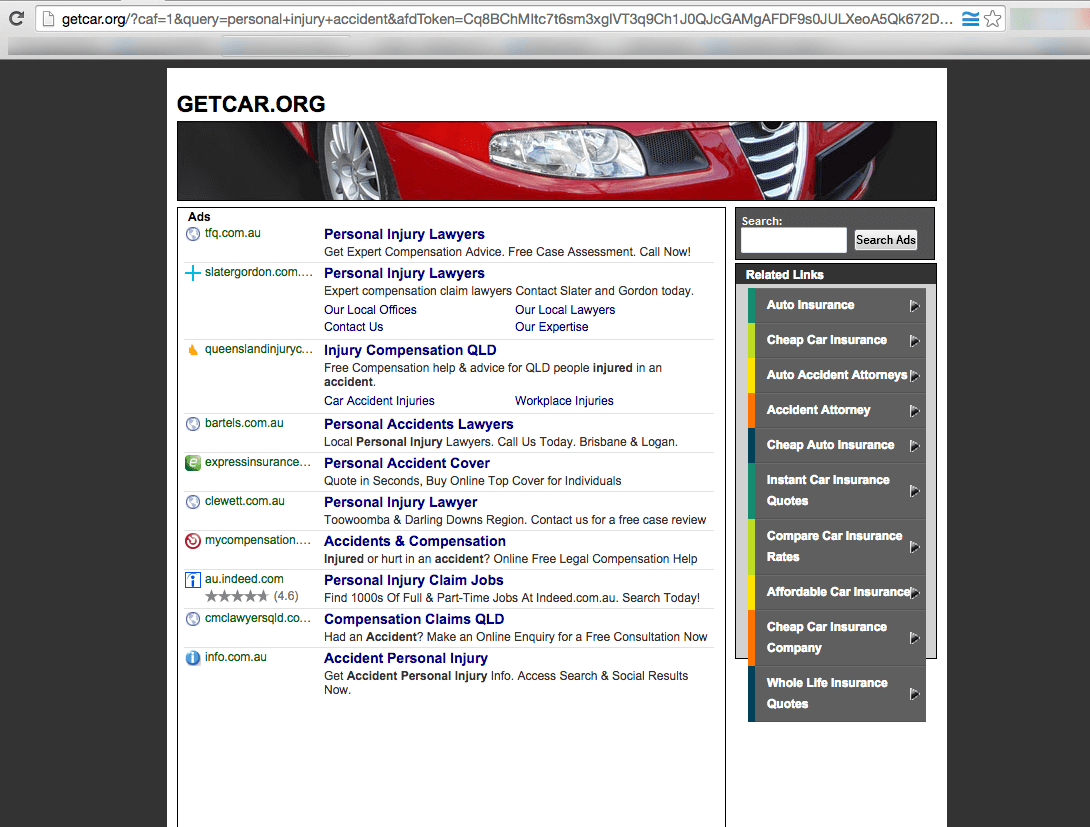
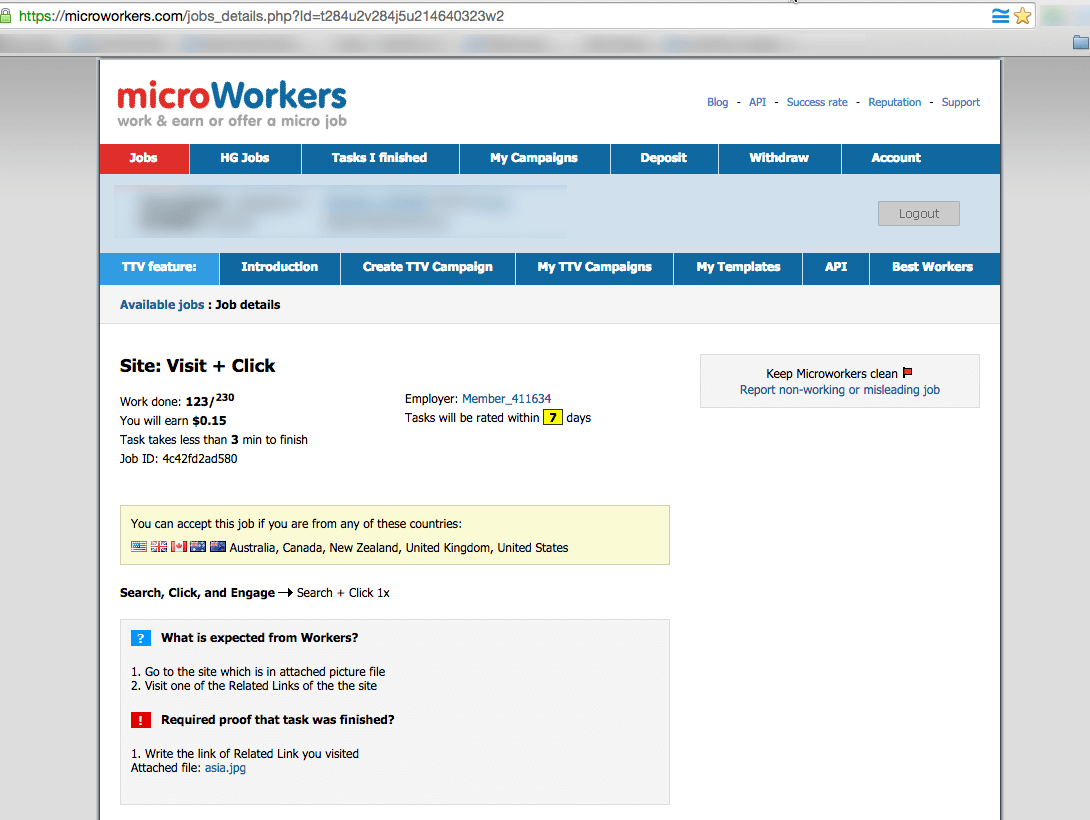
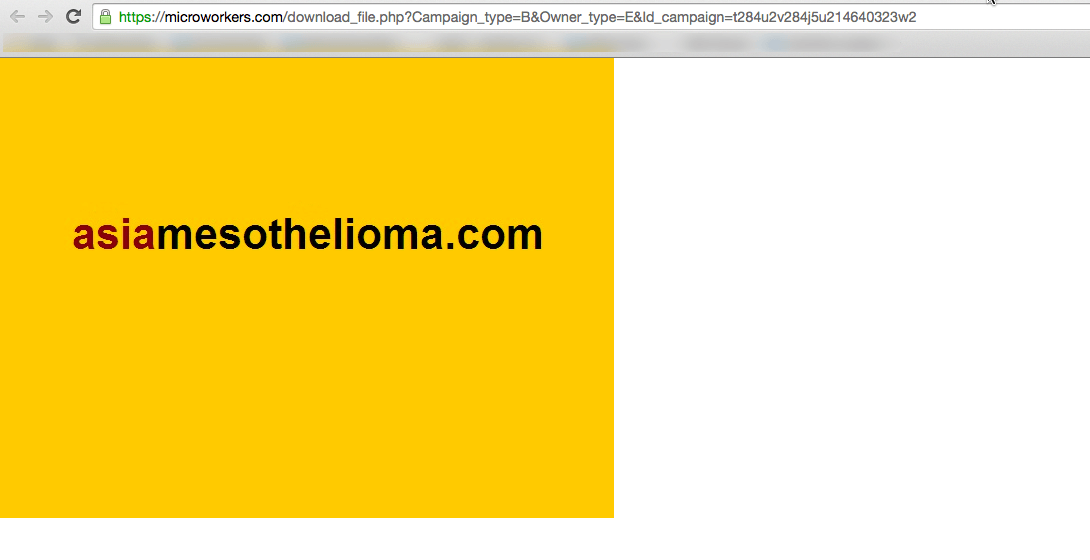
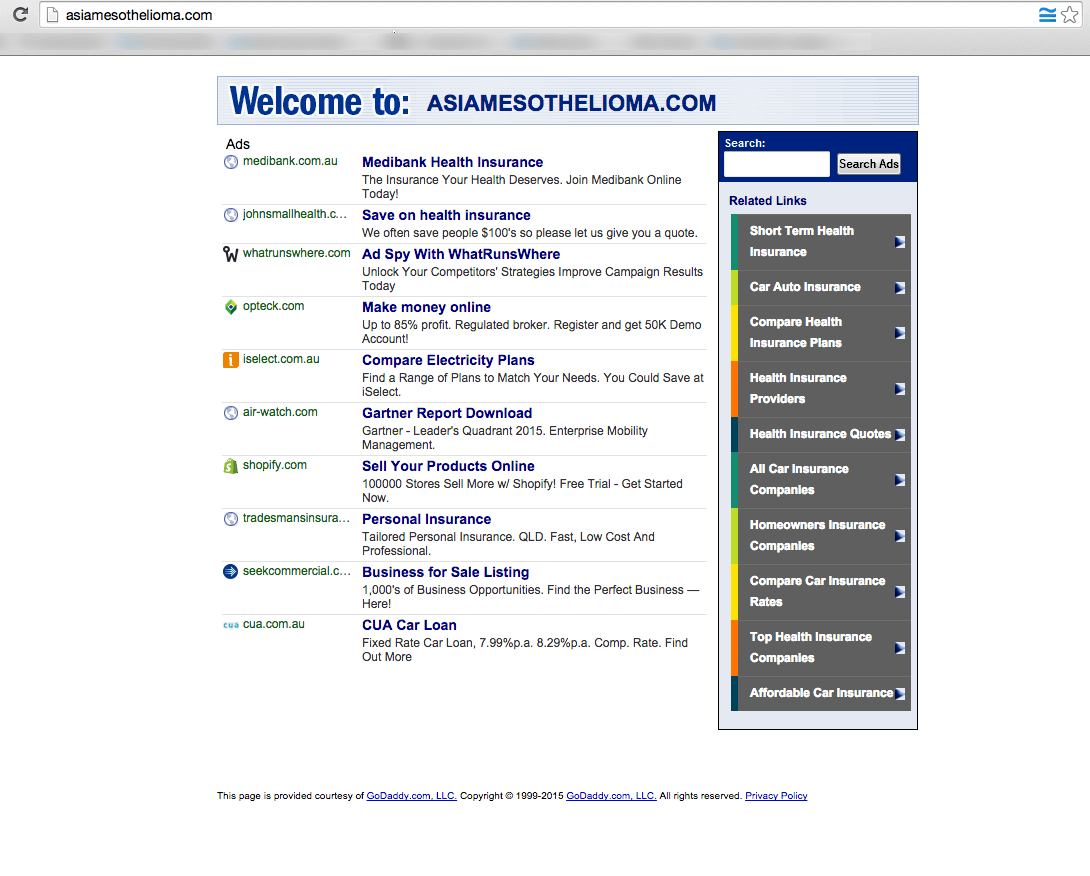
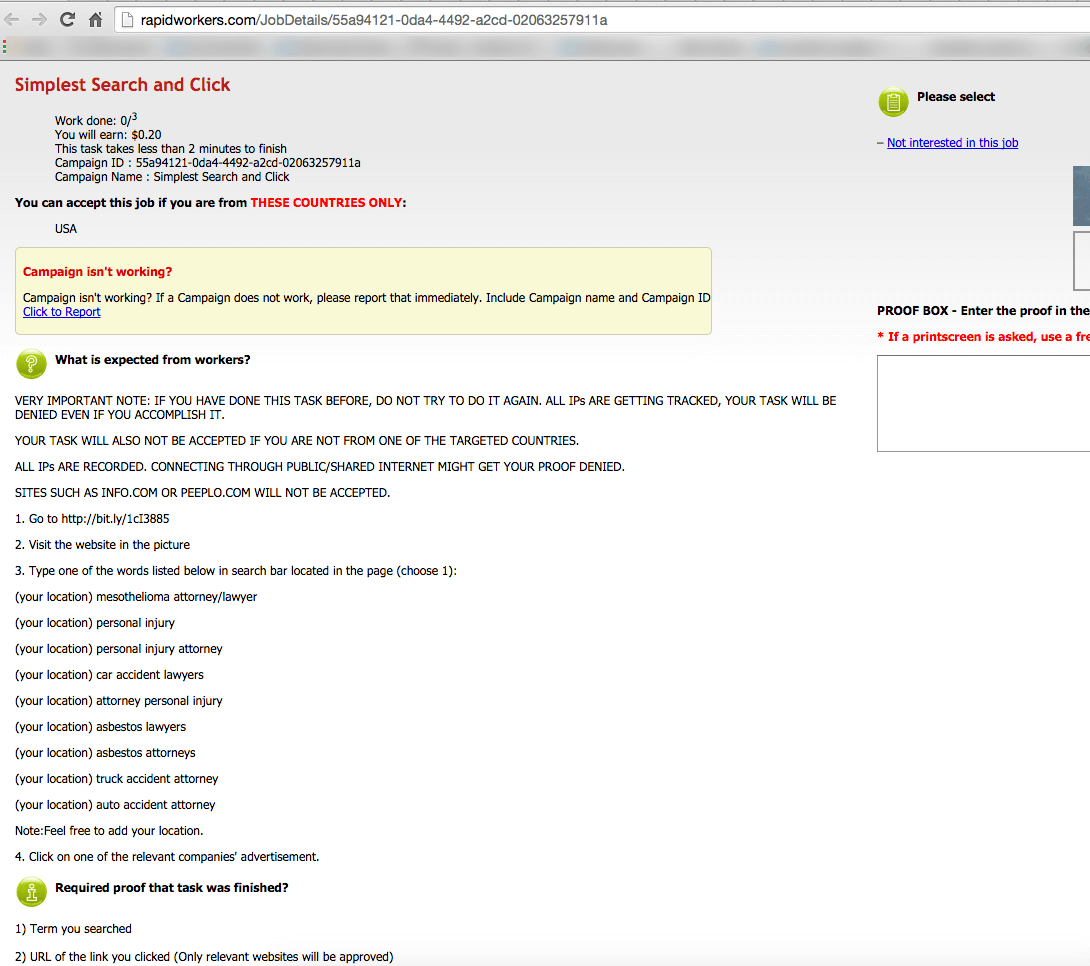
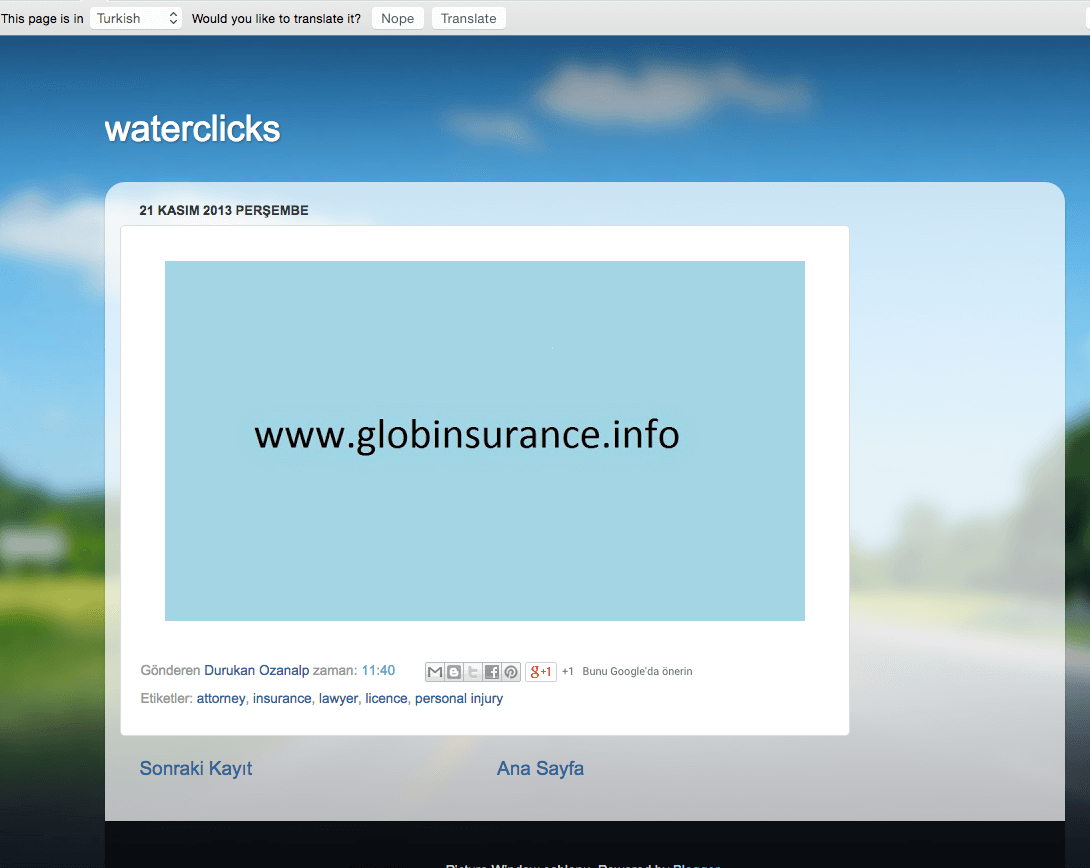
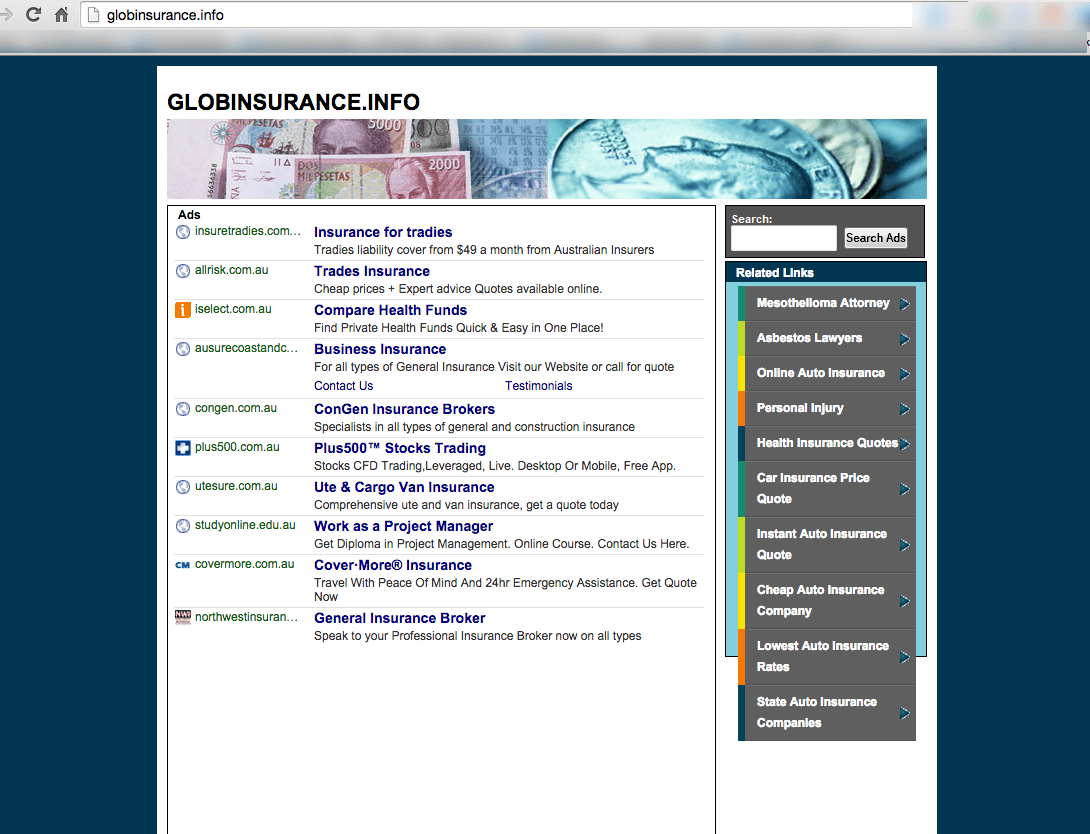
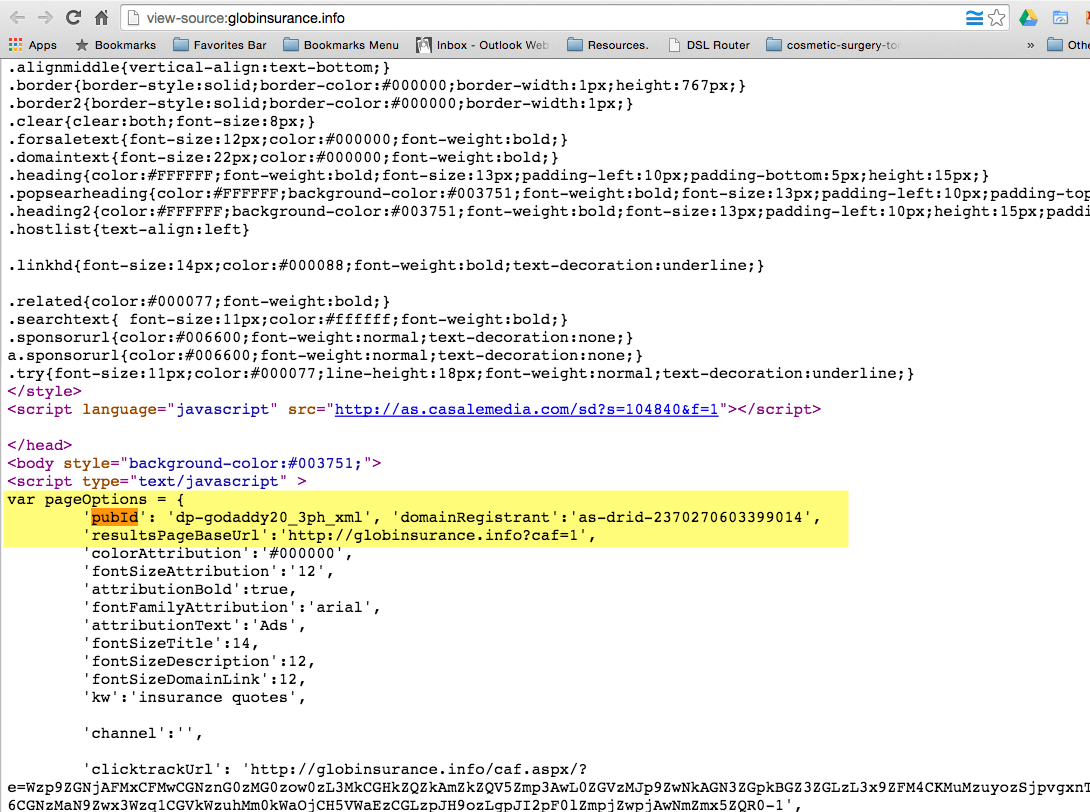
US corporations are enabling fraudulent online theft from Australian and American companies
The scam highlighted above is being done through a service from Godaddy that allows domain name owners to monetize their unused website addresses. The service is called CashParking. Their FAQ describes the service as this:
CashParking® is a service that lets you earn money on your parked domain names. If you associate your domains with your CashParking account, our advertising partner places context-relevant advertisements on your page. Each time a visitor clicks a displayed advertisement, you receive a share of the generated click-through revenue based on your CashParking plan (60% to 80% of the generated revenue). The amount you receive and the price you pay for the CashParking service depends on the plan you select. You can add an unlimited number of domains to your CashParking account.
Parked domains are domains that display a temporary web page when someone enters your domain name in a web browser.
The advertisers on these pages are served primarily by Google and other affiliates of Godaddy. Below is a screenshot of a chat session where a Godaddy employee confirmed that the ads are being served by Google.
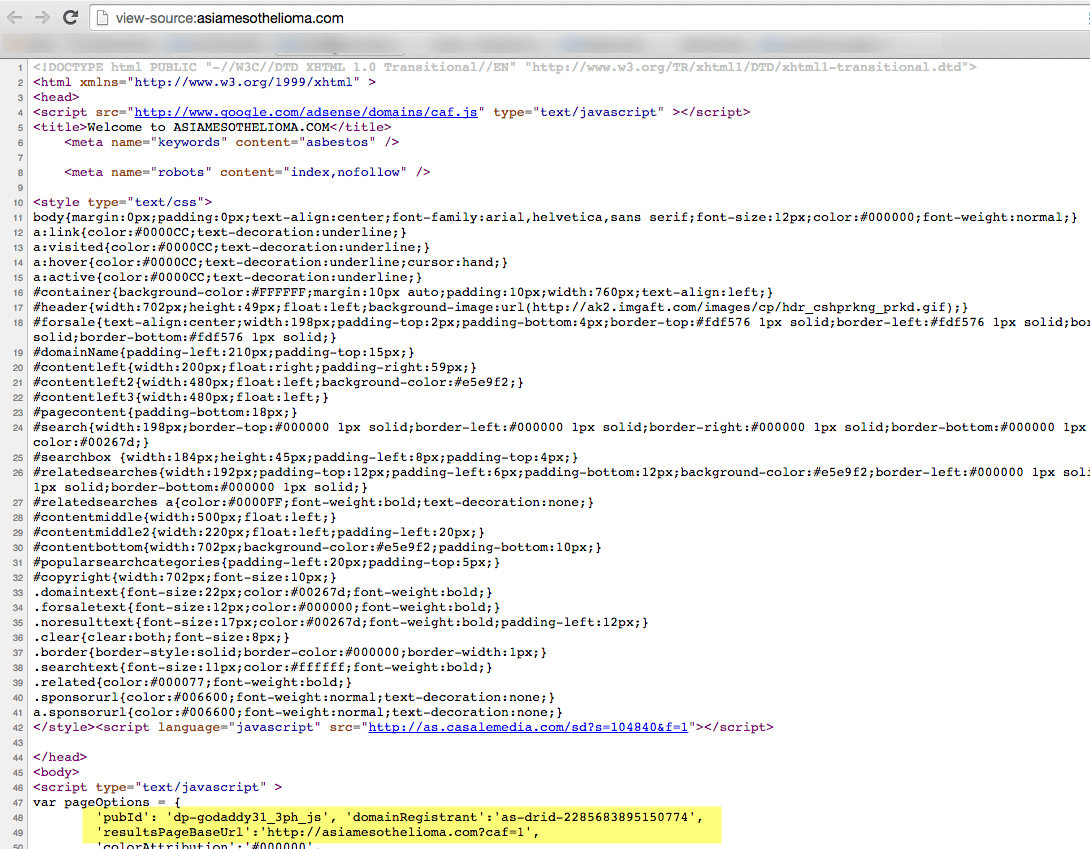
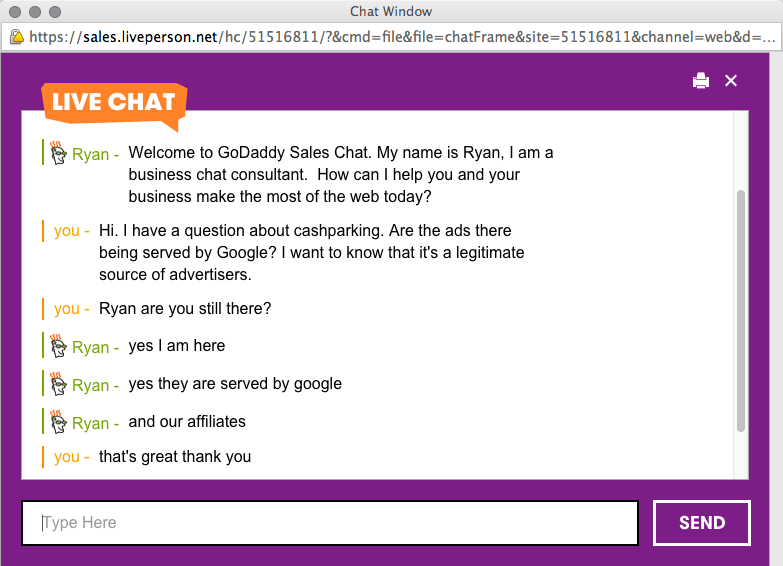
What this means for you as an advertiser is that if you’re paying to serve ads through Google’s search network, you’re likely being exposed to this kind of potential theft.
Since there are other advertising sources involved, it’s unclear exactly where you can advertise safely. Any online ad service that serves ads through these CashParking pages are susceptible to this kind of online theft.
This isn’t to say that these US corporations are aware of what’s going on. But the question has to be asked: are they profiting from this activity on purpose? It’s impossible to know for sure. We use Godaddy services and we’d like to think that they are simply not aware of what is happening in the underground world of blackhat click fraud.
Who is stealing your money?
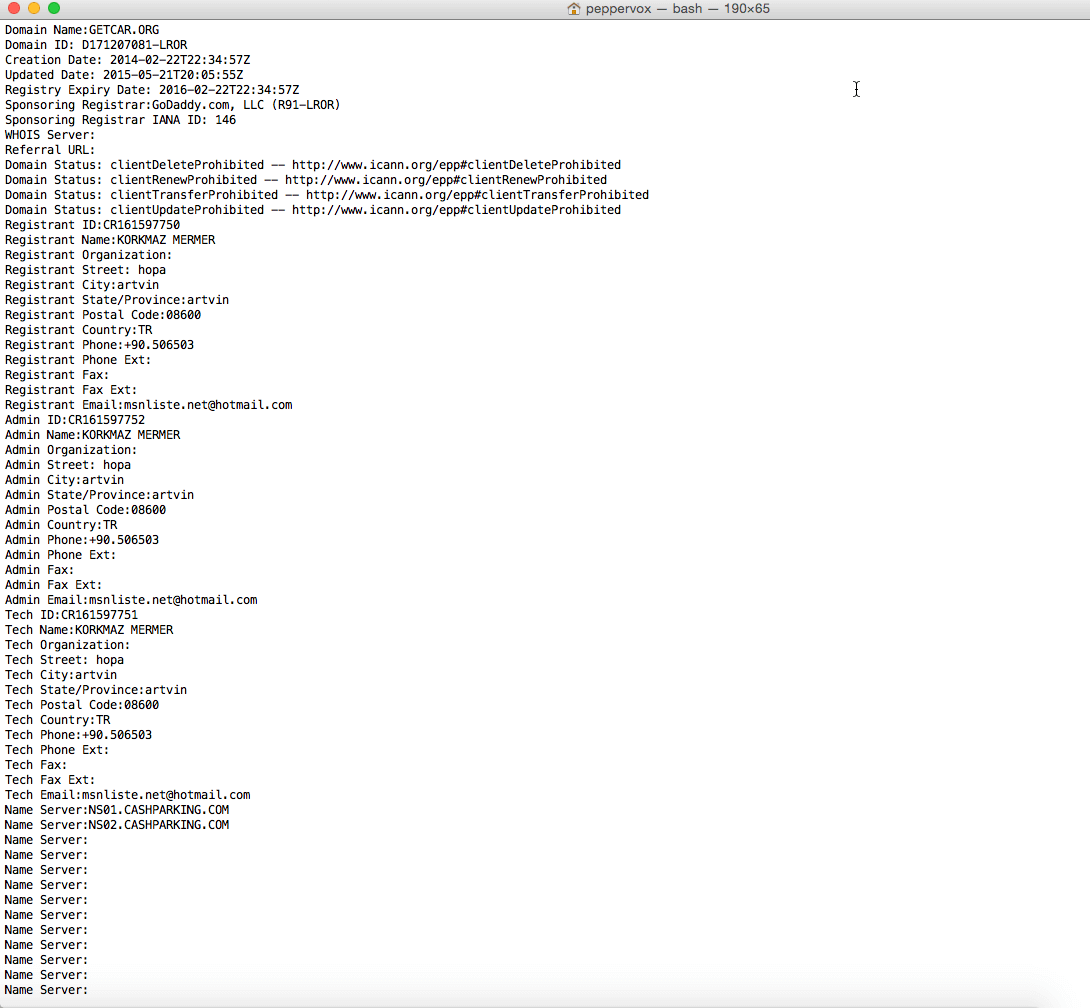
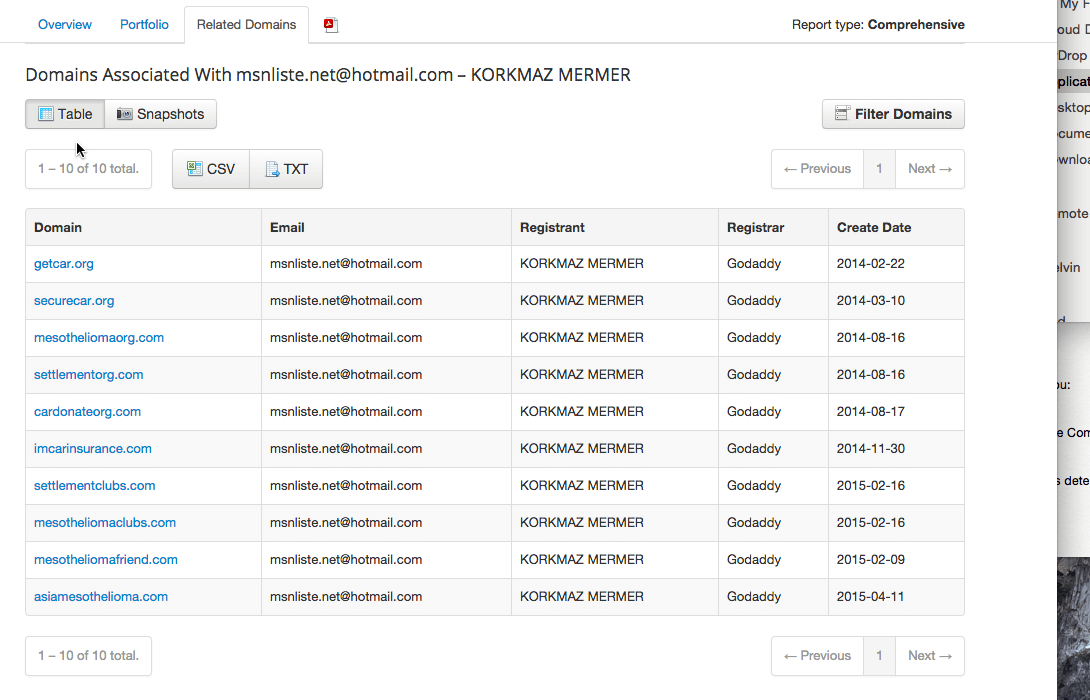
The plot thickened as we dug deeper into the ownership status of the domains behind the scam.
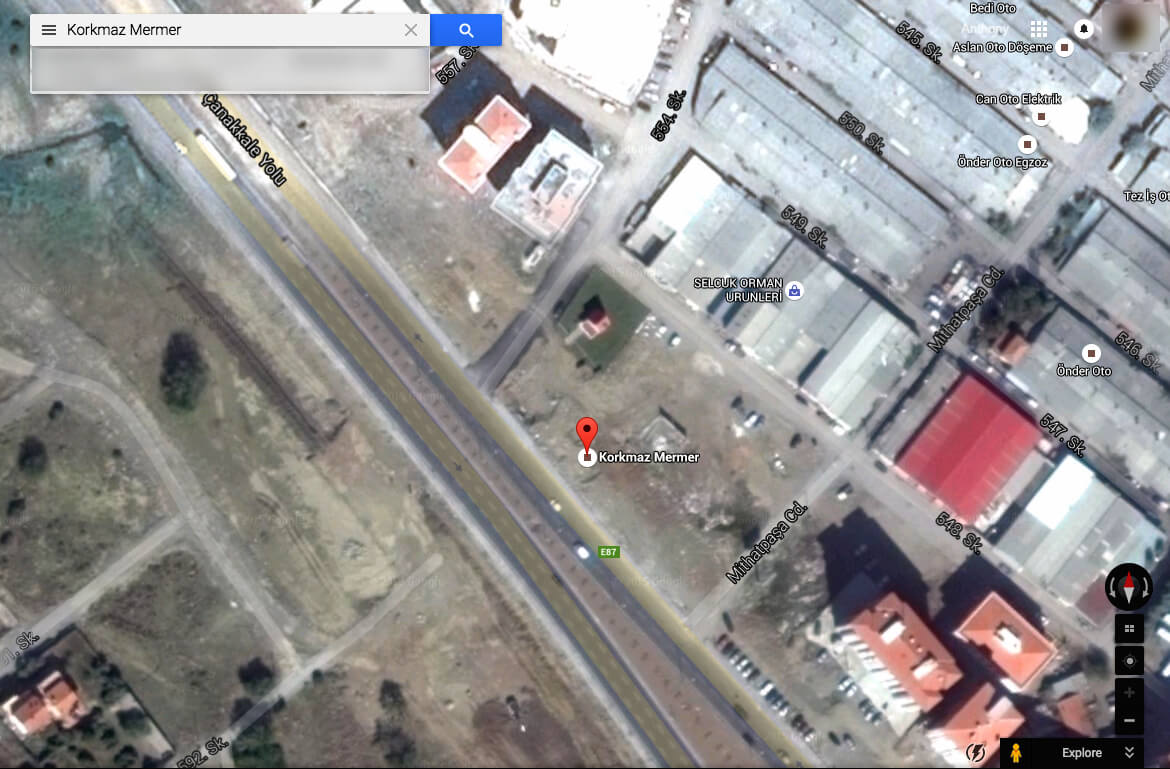
The ownership details for the websites lead to an address in Turkey. The satellite imagery for the address shows an empty lot.
If we follow the apparent money trail, it goes like this:
- Two US corporations are serving ads from global businesses including Australian lawyers and US insurance companies.
- Those companies pay the corporations for the ad clicks.
- The US corporations then send the money to an undisclosed individual in Turkey.
- Once the stolen money arrives in Turkey, it’s anyone’s guess where it goes.
While we’d like to think that the fraudster is simply enjoying his ill gotten gains with a fast car and some delicious Turkish baklava, it’s just as easily converted to cash and transported across the Syrian border to the terrorist groups operating in the area.
If a vacant lot in a foreign country can be used to steal money this easily, the question is why are these large corporations not applying better corporate governance in validating their users’ details?
Why it seems like fraud protection is failing
At about this stage you may be thinking that Godaddy and Google already have fraud protection in place. In fact if you ask them, they would likely tell you all about the stringent measures they use to protect your advertising dollars.
The reason we believe the systems are failing is because of the money in play.
If you understand how criminals work, you understand that they are very good businessmen. Even if you don’t have an understanding of business, you can understand that if a person is not making money with an activity that costs money, that activity is not sustainable. The person would eventually run out of cash, and credit, and would have to stop.
The obvious reason behind our belief that the anti-fraud measure don’t work is simple. The websites above are still actively showing ads. This means that the advertiser's account was not banned. The Microworkers and Rapidworker tasks are active, and we can get paid from running the task. This means that the criminals have money to pay the workers.
Since the account is active, the scam is active, and there is money in play, it seems highly unlikely that any of the fraud mechanisms were effective in curbing this particular scam.
How you can protect yourself from click fraud
Click fraud is a complex topic that would need a series of full articles to discuss in depth. Without getting into the full details of the topic itself, here are some simple things you can do to protect your business against this kind of criminal activity.
Eliminate Google’s search network ads
The first step in protecting yourself is to eliminate all Search Network traffic in Google Adwords. Sites in the Search Network partner with Google to show ads. The examples above are such sites.
Start your advertising campaign by only advertising in Google Search directly until you can put phase two into place. Google Search ads are what you see after you type in a search term in the search engine and get the results page. Because only Google makes money from Google Search ads, you remove the financial incentive for the criminals from the equation. If the conmen don’t have a source of capital, they have no reason to pay workers to click on ads that only make Google money.
Run trackable direct-response ads instead of brand ads
The second step is to start running direct response ads instead of brand ads. Brand advertising is based around exposing people to your business name, or products, without asking the user to take direct action.
In contrast, direct response advertising asks people to take an action on the page which can be tracked and optimized. This action can be anything from filling out your contact form to downloading a free whitepaper, or starting a trial of your service. Any action that can be tracked gives you usable data for phase three.
There is something else called affiliate fraud which involves paying people to fill out your form, but as long as you’re not paying affiliate commissions, you’re safe from that activity. Perhaps we’ll tackle that subject in another article.
Track all activity from your advertising sources and eliminate what’s not working
Now that you’ve set up direct response ads, you can begin adding additional ad sources that are tracked and evaluated in real time.
To do this, you’ll need to set up proper tracking in your Analytics account or other ad monitoring tools. You can start turning on selective traffic sources and evaluating if they convert. If you have a solid direct response offer in place, you will know which sites are sending legitimate traffic and which sites are scams. You eliminate the ad sources that aren’t converting and put your money into the sites that give you real leads, which turn into cash for your business. Any ad source that is ROI positive, you then invest more into.
The key to this is constant vigilance. You need to stay on top of your ads on an ongoing basis — continue to optimize and find new sources that work for your offer. Then wash, rinse, repeat.
Why click fraud is bad for the economy and what corporations could do
Click fraud is like a series of hands reaching into the proverbial economic pocket and pulling money out to be relocated abroad.
It takes cash away from legitimate businesses and cripples them from being able to thrive and create jobs. Because the technology behind the ad services is largely mechanical, even the money the big companies are making is not necessarily reflected proportionally in job creation. Smaller businesses are defrauded on a large scale, which directly impacts local communities.
We admit that this kind of criminal activity is extremely difficult to combat. It would be impossible to eliminate the IP addresses of the real people performing the tasks. The reason is that they’re not defrauding 100% of the time. The microworkers are like you and me. They surf the internet legitimately when they’re not “working” for the crowdsourcing companies. That means that their cookies, user activity, and all other footprints, are legitimate. That’s the reason that the scam works so well.
This doesn’t mean that Godaddy, or Google, are helpless. One key area of governance that’s being overlooked is the validation and certification of the domains. It’s fairly clear to see that the Whois information for the sites is fake. Validating the domain ownership for a company that’s the largest domain registrar in the world should be very achievable.
Criminals are bold because they can hide. If Godaddy, Google, Bing, and all their other ad partners made sure that they’re doing business with real people that are accountable for their activities, the internet would be a much better and safer place. We would also all be a lot more prosperous because advertising spend would return more efficient results with a higher profit for the advertiser. This would then lead to job creation and more legitimate advertising. Everyone would win.
author
:
Anthony Caldwell
Connect with Anthony on Twitter and LinkedIn. Learn more about Anthony on his profile page.
© 2026 Vital+Vectors by PepperVox PTY LTD
disclaimer
:The material on vitalvectors.com is produced by Vital+Vectors. It is intended to provide general information in summary form on relevant topics, current at the time of first publication. The contents do not constitute advice and should not be relied upon as such. Formal advice should be sought in particular matters.
The information and views set out in this article are those of the author(s) and do not necessarily reflect the official opinion of the PepperVox Pty Ltd trading as VitalVectors.com. Neither PepperVox Pty Ltd nor any person acting on their behalf may be held responsible for the use which may be made of the information contained therein.
Reproduction is authorized provided the source is acknowledged.